I. LIMITATIONS
The author acknowledges that this article falls short of a rigorous academic paper. This is explained by the fact that gang stalking and electronic harassment targets are kept in a sort of “barely alive” condition, with significant health problems, and either unable to work or just barely able to hold a job with limited earning potential.
Furthermore, since the perpetrators constantly work to prevent the public from knowing anything about gang stalking and electronic harassment, evidence is obtainable with great difficulty, and often the only evidence is of lower quality than would be accepted for a scientific treatise.
In short, everything in this article represents a struggle against immense odds. We ask readers to understand this and hope that those who are not under electronic attack and surveillance will try through independent channels to find better quality proof.
Up to Contents
II. INTRODUCTION
Electronic harassment and control technology had it's start in the
1950s, as an obscure branch of the CIA's MKULTRA project group.
Just as organized crime is not stopped by hearings and court cases,
neither did this originally obscure branch of MKULTRA activity, when
the institutional/drug/child abuse phases were exposed by the U.S.
Senate's Church-Inouye hearings in the late 1970s. No criminal
proceedings followed, and only two civil law suits (Orlikow and
Bonacci) have succeeded.
This assembly of unclassified and commercial literature is to show
investigators and concerned citizens that in spite of the tightest
possible information blackout imposed in the early 1970s, enough of
the classified electronic harassment and control technology has
leaked out to show that significant classified accomplishments are
overwhelmingly likely, and in need of disclosure, here at the end of
the 20th century.
It is hoped that government and media, who have shied away from this
topic for decades, preferring the warm fuzzy feelings that "this can't
be true", will read about the unclassified and commercial devices and
understand the implications of continued turning the other way.
Up to Contents
III. E-HARASSMENT EFFECTS
Since government-backed electronic harassment and control is classified
at the highest levels in all technologically capapble governments, the
description of effects is taken from the personal experiences of the
"2,000 or so" known gang stalking with electronic harassment targets.
The experimentees without exception report that once the harassment
begins, in virtually all cases it continues for life. It continues in
every city, state, and country the target moves to. It continues in
prisons and hospitals, even when the target is dying of cancer.
Many targets are young seniors, some in their 70s and 80s.
Some have children and the children are often subjected to the same
"testing" as their parent(s). Pets are not only tortured, but even
killed, painfully and violently.
The effects pattern:
This article is about unclassified/commercial technologies which can
produce some of the effects of the harassment equipment:
- All harassment consists of unique, carefully engineered-unprovable
events to produce psychological stress in the victim. There are
no events which do not fit that apparent purpose.
- In every series of stress event type, ONE introductory event of
very high energy/effect is staged. The obvious purpose is to be
certain the victim KNOWS this is external harassment, and not just
"bad luck". From that time forward, the perpetrators appear to
apply "Pavlovian training" so that they can get the victim to "jump"
(or react in some way) to the same effect at a tiny fraction of the
initial "introductory" event.
- This type of harassment started during the Cold War, and shows every
characteristic of military and intelligence psychological warfare
operations.
- This type of harassment points to CONTROL of the test subject.
Endlessly repeated words generated inescapably within the skull
are just one hypnosis-like experience.
- The total number and type of crimes which make up gang stalking and
electronic harassment simply could not take place without cover
being supplied by government. Bizarre court decisions in which the
target is forced into involuntary mental health treatment and a
criminal spouse (for example, a pedophile father discovered "doing"
his own child) clearly show that gang stalking and electronic
harassment are heavily protected by all levels of government and
the medical establishment.
The effect types categorized:
Here is a list of most of the common effects. It is not exhaustive,
but is intended to show the reader how the perpetrators' pallette
of stress effects is broken down. Indent levels are used to show
categories and sub-categories:
1. Invasive At-a-Distance Body Effects (including mind)
a. Sleep deprivation and fatigue
i. Silent but instantaneous application of "electronic
caffeine" signal, forces awake and keeps awake
ii. Loud noise from neighbours, often SYNCHRONIZED
to attempts to fall asleep
iii.Precision-to-the-second "allowed sleep" and "forced
awakening"; far too precise and repeated to be natural
iv. Daytime "fatigue attacks", can force the victim to sleep
and/or weaken the muscles to the point of collapse
b. Audible Voice to Skull (V2S)
i. Delivered remotely, at a distance
ii. Made to appear as emanating from thin air
iii.Voices or sound effects only the victim can hear
c. Inaudible Voice to Skull (Silent Sound)
i. Delivered by apparent at a distance radio signal;
manifested by sudden urges to do something/go somewhere
you would not otherwise want to; silent (ultrasonic)
hypnosis is possible
ii. Programming hypnotic "triggers" - i.e. specific phrases
or other cues which cause specific involuntary actions
d. Violent muscle triggering (flailing of limbs)
i. Leg or arm jerks to violently force awake and keep awake
ii. Whole body jerks, as if body had been hit by large jolt
of electricity
iii.Violent shaking of body; seemingly as if on a vibrating
surface but where surface is in reality not vibrating
e. Precision manipulation of body parts (slow, specific purpose)
i. Manipulation of hands, forced to synchronize with closed-eyes
but FULLY AWAKE vision of previous day; very powerful and
coercive, not a dream
ii. Slow bending almost 90 degrees BACKWARDS of one toe at a
time or one finger at a time
iii.Direct at-a-distance control of breathing and vocal cords;
including involuntary speech
iv. Spot blanking of memory, more than normal forgetfulness
f. Reading said-silently-to-self thoughts
i. Engineered skits where your thoughts are spoken to you
by strangers on street or events requiring knowledge of
what you were thinking
ii. Real time reading subvocalized words, as while the victim
reads a book, and BROADCASTING those words to nearby people
who form an amazed audience around the victim
g. Direct application of pain to body parts
i. Hot-needles-deep-in-flesh sensation
ii. Electric shocks (no wires whatsoever applied)
iii.Powerful and unquenchable itching, often applied precisely
when victim attempts to do something of a delicate or
messy nature
iv. "Artificial fever", sudden, no illness present
v. Sudden racing heartbeat, relaxed situation
h. Surveillance and tracking
i. Rapping under your feet as you move about your apartment,
on ceiling of apartment below
ii. Thru wall radar used to monitor starting and stopping
of your urination - water below turned on and off
in sync with your urine stream
2. Invasive Physical Effects at a Distance, non-body
a. Stoppage of power to appliances (temporary, breaker ON)
b. Manipulation of appliance settings
c. Temporary failures that "fix themselves"
d. Flinging of objects, including non-metallic
e. Precision manipulation of switches and controls
f. Forced, obviously premature failure of appliance or
parts
3. External Stress-Generating "Skits"
a. Participation of strangers, neighbours, and in some cases
close friends and family members in harassment
i. Rudeness for no cause
ii. Tradesmen always have "problems", block your car, etc.
iii.Purchases delayed, spoiled, or lost at a high rate
iv. Unusually loud music, noise, far beyond normal
b. Break-ins/sabotage at home
i. Shredding of clothing
ii. Destruction of furniture
iii.Petty theft
iv. Engineered failures of utilities
c. Sabotage at work
i. Repetitive damage to furniture
ii. Deletion/corruption of computer files
iii.Planting viruses which could not have come from
your computer usage pattern
iv. Delivered goods delayed, spoiled, or lost at a high rate
v. Spreading of rumors, sabotage to your working reputation
vi. Direct sabotage and theft of completed work; tradesmen
often involved and showing obvious pleasure
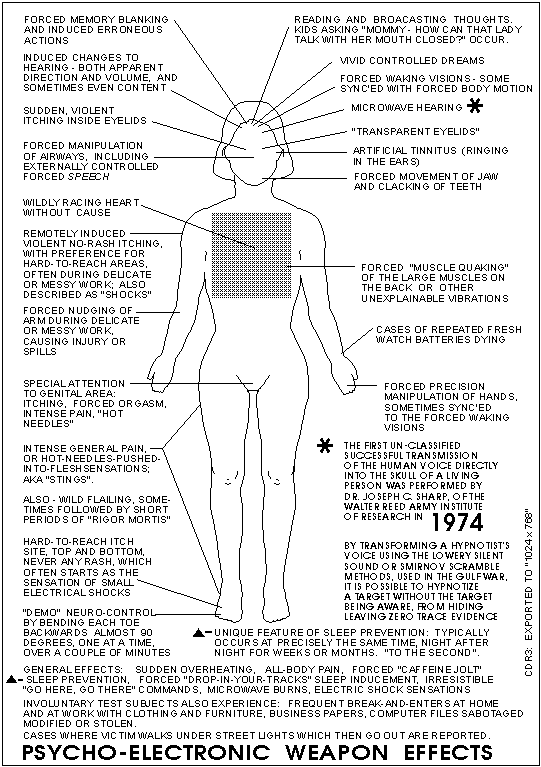
Illustration of the bodily effects
Up to Contents
IV. MAJOR TECHNOLOGY CLASSES
These technology classes are for the UNclassified and commercial
equipment which can emulate the "real" classified electronic
harassment equipment.
Effect section 2, "Invasive Physical Effects at-a-Distance", clearly
establishes the existence of remote precision manipulation of objects
which is far beyond the capabilities of unclassified and commercial
equipment at the time of writing.
REMOTE PHYSICAL MANIPULATION is not covered in this article, but
the reader should know that both NASA and IEEE have noted successes in
creating very small antigravity effects (which are not due to simple
magnetism.)
TRANSMISSION METHODS FOR NEURO-EFFECTIVE SIGNALS:
- pulsed microwave (i.e. like radar signals)
- ultrasound and voice-FM (transmitted through the air)
While transmission of speech, dating from the early 1970s,
was the first use of pulsed microwave, neuro-effective
signals of as yet unknown type can now cause many other
nerve groups to become remotely actuated. At time of
writing, that technology appears to be classified.
PAVLOVIAN HYPNOTIC TRIGGERS:
A [Pavlovian] hypnotic trigger is a phrase or any other
sensory cue which the victim is programmed to involuntarily
act on in a certain way. The 50s-70s MKULTRA survivors can
still be triggered from programming done decades ago. A name
"manchurian candidate", from a novel by John Marks, is used
to describe a person who carries Pavlovian triggers.
One of the main goals of the institutional/drug/child
abuse phases of the CIA MKULTRA atrocities (1950's through
1970's) was to implant triggers using a "twilight
state" (half-conscious) medication and tape recorded
hypnosis. The ultimate goal was to have the acting out
of Pavlovian triggers erased from the victim's memory.
Using a combination of Joseph Sharp voice to skull and
Lowery Silent Sound technologies, these triggers can now
be planted with the subject being unaware, or just barely
aware of a very high tone in his or her hearing sense.
THROUGH-WALL SURVEILLANCE METHODS:
So-called "millimeter wave" scanning. This method uses the
very top end of the microwave radio signal spectrum just
below slightly into the infra-red frequency region. To view
small objects or people clearly, the highest frequency that
will penetrate non-conductive or poorly- conductive walls is
used. Millimeter wave scanning radar can be used in two modes:
- passive (no signal radiated, uses background
radiation already in the area to be scanned,
totally UNdetectable)
- active (low power millimeter wave "flashlight"
attached to the scanner just as a conventional
light mounted on a camcorder), or, the use of
archaeological ground penetrating radar
THOUGHT READING:
Thought reading can be classed as a "through wall
surveillance" technology. Thought reading, in the
unclassified/commercial realm, can be broken down as
follows:
- magnetic skull-proximity or throat (vocal cord
proximity) reading
- EEG (electroencephalogram) interpretation,
particularly by way of inside the brain pickup
wires
The ability to read and display what the eyes are
seeing using implanted pickups is one form of
technology almost the same as "thought reading".
BRAIN ENTRAINMENT:
The reverse of biofeedback. Those low frequency electrical
brain rhythms which are characteristics of various moods
and states of sleep can not only be read out using
biofeedback equipment or EEG machines, but using radio,
sound, contact electrodes, or flashing lights, the moods
and sleep states can be generated or at least encouraged
using brain entrainment devices.
Brain entrainment signals cannot carry voice, which is a
much higher frequency range. Brain entrainment can,
however, be used to "set up" a target to make him/her more
susceptible to hypnosis by inducing a relaxed and/or
sleeping state. (This is the same state used by remote
viewers.)
These major technology classes can produce some of the observed
electronic harassment effects, FROM HIDING AND UNDETECTABLY, with the
exception of remote physical manipulation.
IMPLANTATION is sometimes used to assist the above technologies
but with current devices. Implants do not appear to be required,
based on large numbers of people who have had no surgery, no
unexplained wounds, and no missing time.
Diagram showing the overall method, based entirely on unclassified
1974 technology, of how SILENT hypnosis may be transmitted to a
target without the target's being aware. This technique is probably
the most insidious, because it allows months and years of programming
and Pavlovian trigger-setting, while the target cannot resist
because the target can't hear the programming.
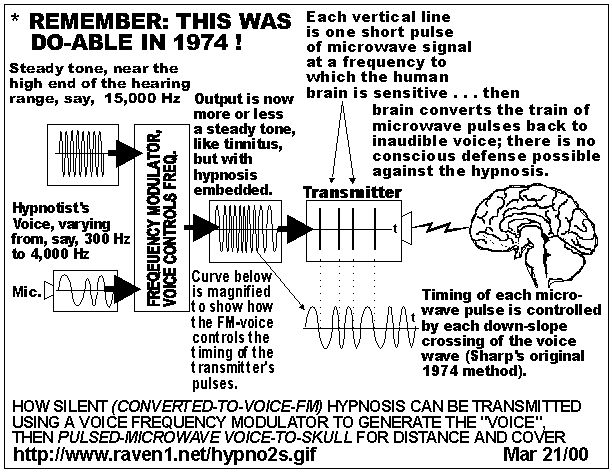
Up to Contents
V. PULSED MICROWAVE
Pulsed microwave voice-to-skull (or other-sound-to-skull) transmission
was discovered during World War II by radar technicians who found they
could hear the buzz of the train of pulses being transmitted by radar
equipment they were working on. This phenomenon has been studied
extensively by Dr. Allan Frey, whose work has been published in a number
of reference books.
What Dr. Frey found was that single pulses of microwave could be heard
by some people as "pops" or "clicks", while a train of uniform pulses
could be heard as a buzz, without benefit of any type of receiver.
Dr. Frey also found that a wide range of frequencies, as low as 125 MHz
(well below microwave) worked for some combination of pulse power and
pulse width. Detailed unclassified studies mapped out those frequencies
and pulse characteristics which are optimum for generation of "microwave
hearing".
Very significantly, when discussing electronic harassment, is the
fact that the PEAK PULSE POWER required is modest - something like
0.3 watts per square centimeter of skull surface, and this power level
is only applied for a very small percentage of each pulse's cycle time.
0.3 watts/sq cm is about what you get under a 250 watt heat lamp at
a distance of one meter. It is not a lot of power.
When you take into account that the pulse train is OFF (no signal) for
most of each cycle, the average power is so low as to be nearly
undetectable.
Frequencies that act as voice-to-skull carriers are not single freq-
uencies, as, for example TV or cell phone channels are. Each sensitive
frequency is actually a range or "band" of frequencies. A technology
used to reduce both interference and detection is called "spread
spectrum". Spread spectrum signals have the carrier frequency "hop"
around within a specified band.
Unless a receiver "knows" the hop schedule in advance, there is virtually
no chance of receiving or detecting a coherent readable signal. Spectrum
analyzers, used for detection, are receivers with a screen. A spread
spectrum signal received on a spectrum analyzer appears as just more
"static" or noise.
My organization was delighted to find the actual method of the first
successful UNclassified voice to skull experiment in 1974, by Dr.
Joseph C. Sharp, then at the Walter Reed Army Institute of Research.
Dr. Sharp's basic method is shown in Appendix PM6, below. A Frey-
type audible pulse was transmitted every time the voice waveform
passed down through the zero axis, a technique easily duplicated by
ham radio operators who build their own equipment.
A pattern seems to be repeated where research which could be used for
mind control starts working, the UNclassified researchers lose funding,
and in some cases their notes have been confiscated, and no further
information on that research track is heard in the unclassified press.
Pulsed microwave voice-to-skull research is one such track.
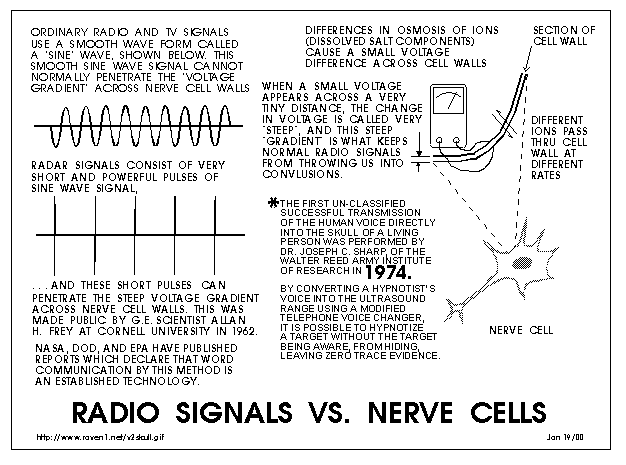
Illustration showing the principle behind pulsed microwave voice-to-skull
Appended articles:
PM1 http://www.raven1.net/lida.htm, photo and description of
the old medical device, the Korean War vintage LIDA machine, a
radio frequency BRAIN ENTRAINMENT device developed by Soviet Russia
as a drugless tranquilizer. BRAIN ENTRAINMENT IS INCLUDED IN THE
RADIO FREQUENCY SECTION BECAUSE THE MOST INSIDIOUS METHOD OF BRAIN
ENTRAINMENT IS TO SILENTLY USE RADIO SIGNALS.
PM2 http://www.raven1.net/frey.htm, Human Auditory System Response
To Modulated Electromagnetic Energy, Allan H. Frey, General Electric
Advanced Electronics Center, Cornell University, Ithaca, New York
PM3 http://www.raven1.net/v2s-nasa.htm, NASA technical report
abstract stating that speech-to-skull is feasible
PM4 http://www.raven1.net/v2s-kohn.htm, DOD/EPA small business
initiative (SBIR) project to study the UNclassified use of voice-to-
skull technology for military uses. (The recipient, Science and Engin-
eering Associates, Albuquerque NM, would not provide me details on the
telephone)
PM5 http://www.raven1.net/bioamp.htm, Excerpts, Proceedings of
Joint Symposium on Interactions of Electromagnetic Waves with
Biological Systems, 22nd General Assembly of the International
Union of Radio Science, Aug 25 - Sep 2, 1987, Tel Aviv, Israel
SHOWS BIOLOGICAL AMPLIFICATION OF EM SIGNALS, pointing to relative
ease with which neuro-electromagnetic signals can trigger effects
PM6 http://www.raven1.net/v2succes.htm, Excerpt, Dr. Don R.
Justesen, neuropsychological researcher, describes Dr. Joseph C.
Sharp's successful transmission of WORDS via a pulse-rate-
modulated microwave transmitter of the Frey type.
PM7 http://www.raven1.net/russ.htm, FOIA article circulated among
U.S. agencies describing the Russian TV program "Man and Law",
which gives a glimpse into the Russian mind control efforts.
(Dr. Igor Smirnov, a major player, was used as a consultant to
the FBI at the Waco Branch Davidian standoff.)
Up to Contents
VI. ULTRASOUND AND VOICE-FM
Ultrasound is vibration of the air, a liquid, or a solid, above the
upper limit of human hearing which is roughly 15,000 Hz in adults.
Voice-FM uses a tone at or near that upper limit, and the speaker's
voice VARIES the frequency slightly. Either a "tinnitus-like sound"
or nothing is heard by the target.
Ultrasound/voice-FM can be transmitted in these ways:
- directly through the air using "air type transducers"
- directly to the brain using a modulated microwave pulse train
- through the air by piggybacking an ultrasound message on top
of commercial radio or television
The use of commercial radio or television requires that the input signal
at the transmitter be relatively powerful, since radio and TV receivers
are not designed to pass on ultrasound messages. However, the average
radio and TV receiver does not simply stop ultrasound, rather, the ability
to pass ultrasound messages "rolls off", i.e. decreases, as the frequency
is increased.
Today's radios and TVs can carry enough ultrasound messaging to be "heard"
by the human brain (though not the ear) to be effective in conveying
hypnosis. This was proven by the U.S. military forces in the Gulf War.
Ultrasound's (and voice-FM's) main advantage in mind electronic harassment
work is that it can carry VERBAL hypnosis, more potent than simple
biorhythm entrainment.
The brain CAN "hear" and understand this "inaudible voice", while the ear
and conscious hearing cannot. Once you can convey hypnotic suggestion
which cannot be consciously heard, you have eliminated a major barrier to
the subject's acceptance of the words being transmitted.
In previous decades, "subliminal advertising" using voice and images at
normal frequencies were "time sliced" into an apparently normal radio or
TV broadcast. This apparently did not work well, and now voice-FM
"subliminal learning tapes" commercially available have superseded the
old time slice method.
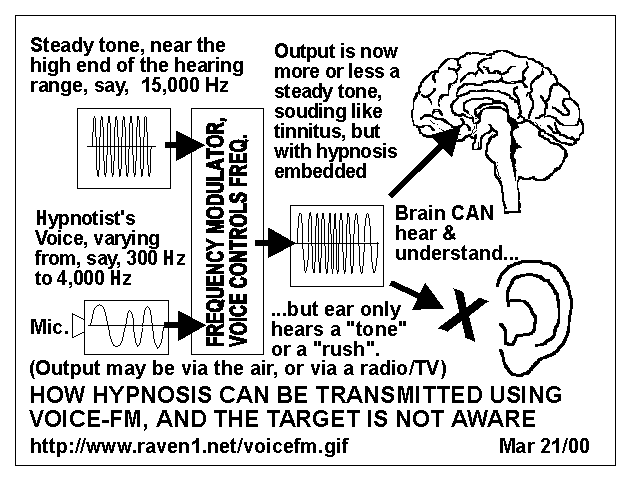
Illustration showing the operation of "silent sound" with the human
hearing system, using near-ultrasound, FREQUENCY MODULATED voice
One method for projecting either audible voice or voice-FM over long distances, virtually undectable if line of sight, is the "acoustic heterodyne" or "HyperSonic Sound" system, patented by American Technologies Corporation, San Diego CA, http://www.atcsd.com
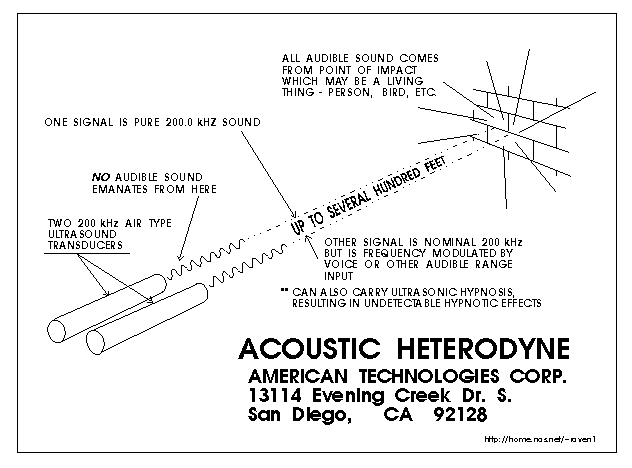
Illustration showing the principle of an ultrasound projection system
capable of true ventriloquism at a distance, by American Technologies
Corporation (licensor), Akai Japan (licensee)
Appended articles:
US1
http://www.raven1.net/silsoun2.htm, ITV Silent Sound report
with comments by Judy Wall, Editor, Resonance, newsletter of MENSA's
bioelectromagnetic special interest group
US2
http://www.raven1.net/commsolo.htm, an article by Judy Wall
outlining instances of UNclassified, openly-admitted-to, electronic
mind control operations by government agencies.
US3
http://www.raven1.net/armyparw.htm, an SBIR (small business
initiative contract) which clearly shows intent to use ultrasound as
an anti-personnel weapon, including one-man portability and with power
to kill
US4
http://www.raven1.net/ssnz.htm, a commercial New Zealand company,
Altered States Ltd., sells tapes which perform "suggestions" (i.e.
hypnosis but not called such) using the Lowery patent voice-FM
method, to hypnotize without the subject being aware. This is a key
feature of neuro-electromagnetic involuntary experiments.
US5
http://www.raven1.net/acouspot.htm, a page originally from the
MIT Media Lab's acoustic engineer, Joseph Pompeii. Describes a similar
technique under commercial and military development (American Techno-
logies Corp., San Diego) under the trade name "Hypersonic Sound".
Shows that sound can be focussed to the extent of targetting just one
person in a crowd, acoustically, using ultrasound.
Up to Contents
VII. THROUGH-WALL RADAR
When "millimeter wave" microwave signals are received, the waves are so
small that they can display a two-dimensional outline of an object. Lower
frequency radar can only show a "blip" which indicates an object's presence
or motion, but not it's outline.
Incoming millimeter wave signals are channeled on to a plate with a two-
dimensional array of elements sensitive to millimeter wave frequencies, in
exactly the same way a camcorder focusses light on to array of sensitive
light pickups. Each of the sensitive elements is scanned in a definite
order, just as with a TV camera and screen, and a picture showing the
outline of an object is formed.
If no signal is sent out by the scanner, it is called "passive" millimeter
wave radar. If the subject is illuminated by a separate source of
millimeter wave signals, it is an "active" scanner. Since passive systems
can penetrate clothing and non-conductive walls UNDETECTABLY, it is obvious
that with just a small millimeter wave "flashlight", non-conductive walls
can be scanned through and still very little detectable signal is present.
Millimeter wave through-clothing, through-luggage is currently in use
at airports, but can be a powerful tool for stalking gangs wishing to
harass a target at home.
The subject is portrayed in the nude.

Appended articles:
TWR1
http://www.raven1.net/lads.htm, LADS, Life Assessment Detector
System, a product of VSE Corporation, can scan through more than
a hundred feet of non-conductive or poorly-conductive material to
detect a beating human heart
TWR2
http://www.raven1.net/nij_p44.htm, Prototype version of the
"radar flashlight", which is a more portable version of the LADS
system above. Can also be used to illuminate a subject for use
with a Millivision thru-clothing/thru-nonconductive wall scanner
TWR3
http://www.raven1.net/millitec.htm, October 1995 blurb from
Popular Mechanics, with photos showing hidden guns used for demo
purposes (Millitech sold the rights to Millivision)
TWR4
http://www.raven1.net/psradar.htm, March 22 text taken from
Patriot Scientific Corporation's web site, their ground-penetrating
radar section. Patriot's GPR overcomes the limitation of the
Millivision passive radar, i.e. inability to penetrate partially
conductive walls.
Up to Contents
VIII. THOUGHT READING
"Thought reading", at least of words "silently said-to-self", appears to
be not that difficult to do. NASA is experimenting with sensitive
pickup coils on the throat of a pilot, for example.
Thought reading by way of pickup wires or coils on the head is an enhanced
version of computer speech recognition, with EEG waves being substituted
for sound waves.
The easiest "thought" reading is actually remote picking up of the electro-
magnetic activity of the speech-control muscles in the vocal cords.
When we "say words to ourselves, silently", or, read a book, we can actually
FEEL the slight sensations of those words in our vocal muscles - all that is
absent is the passage of air. Coordinated speech signals are relatively
strong and relatively consistent.
The other kind of "thought reading", i.e. "MINING" someone's brain for
information from a distance is SPECULATIVE. We targeted individuals have
no way to verify that is happening, however, we do know that we are "fed"
hypnotic signals to force consistent "neutral" content (but of different
character than prior to becoming test subjects,) DREAMS.
These forced, neutral content ("bland" content) dreams occur every single
night and may represent the harassers' (or experimenters') efforts to have
our experiences portray themselves in such dreams, in effect, MINING our
experiences. Again, this is SPECULATION, but it seems very logical.
Appendix TR4, referenced below, confirms the ability of current unclassified
technology to actually see what a living animal sees, electronically. It is
therefore extremely likely that these forced dreams can be displayed on the
experimenters' screens.
Finally, among the "couple of thousand" known gang stalking and electronic
harassment, we sometimes have strangers either tell us what we are thinking,
say they can pick up our broadcast thoughts, or tell us about events inside
our homes at times when they could not have seen from the outside. BUGS
and covert cameras are not used, and they have been searched for.
Appended articles:
TR1
http://www.raven1.net/thotuncl.htm, Commercially available
thought-reading devices, both implant-style and non-implant
TR2
http://www.raven1.net/ratrobot.htm, Implanted rats can control
devices with their thoughts
TR3
http://www.raven1.net/ebrain.htm, from the July 1973 issue of
Popular Electronics, a system to read EEG signals (the stuff of which
thought reading is made) at a distance by passing a radio signal through
the human head and analyzing the passed-through signal. THIS IS NOT
PROVEN TECHNOLOGY but it is one experimenter's suggestion.
TR4
http://www.raven1.net/elecvisn.htm, an article describing
electronically reading a cat's brain waves and constructing a real-time
image on screen from the EEG traces
TR5
http://www.raven1.net/m_switch.htm, the text from a site describing
a mind-controlled "switch", which can not only turn appliances on or off,
but also adjust controls like volume.
Up to Contents
IX. IMPLANTS
Electronic implants are actually one of the older forms of electronic mind
control technology. Implants can either receive instructions via radio
signals, passing them to the brain, or, can be interrogated via external
radio signals to read brain activity at a distance.
Implants are currently used, however, many of our group have had no
surgery, unexplained wounds, or missing time since becoming targets, and
we suspect that both implant and non-implant technology may be in use.
Implants are significant for these reasons:
1. Their use, since World War II and continuing to the present day,
associated with MKULTRA atrocities, is a crystal clear indication
that a MOTIVE POOL of unethical researchers has existed through
the late 1970s. The same people, none jailed, are still working,
by and large. The reader can see that the existence of the same
motive pool is overwhelmingly likely, given that no social changes
have occurred which would prevent that.
2. The fact that to date (autumn 1999) no victim who has had implants
removed has ever been able to get custody of the removed implant
shows that research programmes using implants are still quite active
and obviously quite important to someone. Implants, even though
not in the hands of the victim, were photographed and are quite
real:
See http://www.ritualabuse.net/MCF/,
the Mind Control Forum for details on involuntary experimentees'
implantation and removal experiences.
3. The use of implants shows that, in the field of involuntary human
experimentation, not every perpetrator group has access to the
most sophisticated (implant-less) technology. Since implants for
beneficial purposes are actively being promoted by NIH, it is
obvious they will not disappear any time soon.
Appended articles:
IMP1
http://www.raven1.net/centneur.htm, an article showing that
human implantation is being done and even encouraged by the U.S.
NIH (National Institutes of Health). While this public information
is for the public good, it is a small step to move from publicly
known and VOLUNTARY implantation to CONCEALED implantation for
INvoluntary and criminal purposes.
IMP2
http://www.raven1.net/italydoc.htm, a testimonial by an
Italian psychiatrist who has been assisting involuntary experimentees;
this doctor began by assisting [Satanic or other] ritual abuse victims.
Apparently involuntary brain implantation is alive and well in Italy,
why not elsewhere?
IMP3
http://www.raven1.net/telectro.htm, a project abstract by
AF, awarded to perform unclassified research and development of human
implants which can read both physio- and PSYCHO- parameters.
IMP4
http://www.raven1.net/stimocvr.htm, an excerpt describing
human implantation for purposes of two-way communication with the brain
by way of implants and FM VHF radio. Blows away any doubts that human
implantation has not been done, and even more, that the U.S. military
are involved.
IMP5
http://www.raven1.net/sattrack.htm, describes an unclassified
human implant satellite tracking system, ostensibly for benevolent use.
(No method for avoiding unethical uses is described.) Applied Digital
Solutions, Inc., Palm Beach, Florida.
Up to Contents
X. CONCLUSION
Conclusion? While the documentary evidence in this report, attached as
appendices below, does not exactly "prove" we are being targeted by
intelligence/defense contractors using classified electronic weapons, it
certainly eliminates the argument that such devices are impossible, don't
exist, or that government has "no interest" in them, or that the "were
tried years ago but didn't work".
Add in the experiences of victims of the Tuskegee untreated syphilis exper-
iments, the feeding of radioactive food to uninformed U.S. citizens, and
the atrocities perpetrated under the institutional/drug/child abuse phases
of the CIA's MKULTRA programmes, and you have more than enough grounds to
petition for an independent, open investigation of electronic harassment
capable technologies.
No doubt there were citizens of ancient Pompeii who argued that Vesuvius
could not possibly erupt in their lifetimes.
Eleanor White
If any doubts as to the importance of this issue remain, please see below
what the U.S. NSA (National Security Agency) says would be the result of
releasing information on electronic mind control, which is one motive
for developing weapons which can be used for electronic harassment:

Up to Contents
|








Replies