Nashville,TN
Ernesto Rodriguez's Posts (9)
WikiLeaks accepts classified, censored or otherwise restricted material of political, diplomatic or ethical significance. WikiLeaks does not accept rumour, opinion or other kinds of first hand reporting or material that is already publicly available.
Submitting confidential material to WikiLeaks is safe, easy and protected by law.
We have several methods, but the best for most submissions is:
Click here to securely submit a file online
(bank grade encrypted submission, no logs kept and protected under Swedish and Belgium press secrecy laws)
You can also use secure TOR network
(secure, anonymous, distributed network for maximum security)
Join our chat and we will answer any questions or problems you might have
Our chat is secure and anonymous. Visitors are protected on many layers, they can't see each other,
there is an anti-logging mechanism in place and the server forbids using any potentially dangerous commands that could reveal other user's identity.
Communication is secured with SSL encryption.
Over 100,000 articles catalyzed world-wide. Every source protected. No documents censored. All legal attacks defeated.
| Emerging Picture of War in Iraq and Afghanistan from Wikileaks Files: Devastating |  |  |  |
| Monday, 26 July 2010 16:11 | |
Wikileaks.org, over the past few months, has released some of the most damning evidence yet against theongoing occuptions in Iraq and Afghanistan.Collateral Murder (released April 5, 2010)Collateral Murder is the military's own video of 12 Iraqis being shot and killed from a UShelicopter circling above. No one has been charged in connection withthese killings. However, 22 yr. old Pfc. Bradley Manninghas been held incommunicado on military bases for several months now,suspected of leaking this incriminating video to Wikileaks. World Can'tWait is distributing copies of this harrowing video so that many morepeople in the US see what is being done in their names. For a copy, write to us. More: How to Show "Collateral Murder" Outside in Public Ethan McCord: Memories of “Collateral Murder” - by Someone who was There Anthony Wagner: Collateral Murder
Afghan War Diary (released July 26, 2010)Wikileaks released 76,000 military records exposing the truth of the unjust, illegitimate war in Afghanistan: revealing hundreds of civiliandeaths, execution squads, other war crimes. They have 15,000 morerecords from Afghanistan that they are holding back for the timebeing. For more on the developing picture emerging, see The Afghanistan War Logs on the Guardian UK and Wikileaks.org (both are being regularly updated). If Wikileaks is down, it may be overloaded. To see the files, go directly to wardiary.wikileaks.org. Webcast: Anti-War Leaders and Veterans Respond to the WikiLeaks Revelations (recorded August 1, 2010)Watch recording now: www.livestream.com/worldcantwait World Can't Wait presents a national webcast of anti-war leaders and veterans responding to the WikiLeaks revelations. What should we doNOW, immediately to end the occupations of Afghanistan & Iraq?
Julian Assange on the Afghan War Logs: "They Show the True Nature of this War"Democracy Now! July 26thThe New Pentagon Papers: WikiLeaks Releases 90,000+ Secret Military Documents Painting Devastating Picture of Afghanistan War With independent British journalist Stephen Grey; Pentagon Paperswhistleblower, Daniel Ellsberg; former State Department official inAfghanistan, Matthew Hoh; independent journalist Rick Rowley; andinvestigative historian Gareth Porter. Democracy Now! July 28thWe spend the hour with Julian Assange, the founder of WikiLeaks, talkingabout the biggest leak in US history: the release of more than 91,000classified military records on the war in Afghanistan. Democracy Now! August 3rdJulian Assange Responds to Increasing US Government Attacks on WikiLeaks Further Coverage:Watch Julian Assange at press conference July 26. Kevin Gosztola: Nearly 92,000 Classified Documents Leaked, Expose Truth of Afghan War Wikileaks files 'may reveal thousands of war crimes' (Independent.co.uk) US condemns Wikileaks: Julian Assange says "this is the story of the war" (BBC) Chris Floyd: Leaky Vessels: Wikileaks "Revelations" Will Comfort Warmongers, Confirm Conventional Wisdom Jason Ditz: Pentagon Launches ‘Manhunt’ for Document Leaker Kenneth J. Theisen: Use the WikiLeaks Afghan War Diary to Mobilize Resistance to the U.S. War of Terror Kevin Gosztola: The Danger of the Wikileaks' Leak: You Might Stop Thinking Like an American Cindy Sheehan: I Have Become Uncomfortably Numb Debra Sweet: More War Crimes Exposed - Now, What Do We Do? Revolution editorial: WikiLeaks: Exposing War Crimes of a Criminal War |
We Stand With Bradley Manning
 If Bradley Manning is the sources of any or all of the recentinformation about Afghanistan and/or the "Collateral Murder" videoreleased by Wikileaks, he is a hero. Whether or not he is the leaker,he should be released immediately.
If Bradley Manning is the sources of any or all of the recentinformation about Afghanistan and/or the "Collateral Murder" videoreleased by Wikileaks, he is a hero. Whether or not he is the leaker,he should be released immediately.
For more background information, see Wikileaks reveals video showing US air crew shooting down Iraqi civilians and Army Intelligence Analyst Charged for Releasing Wikileaks Video: Killers Remain Free
Also see: bradleymanning.org where you can donate to his legal defense.
Join savebradley on Facebook
Write to Bradley with your support:
Inmate Bradley Manning
USMC Base Quantico Brig
3247 Elrod Avenue
Quantico, VA 22134
Sign on to this statement of support:
| Before the Protests Tommorrow at Fort Hood |  |  |  |
| Saturday, 21 August 2010 19:12 |
I am in Killeen, TX at Under The Hood Cafe near the Fort Hood military base tonight. I am down here for the protests happening onSunday being called by the Disobedient. The Disobedient is made up of Iraq era war vets and others anti- war activists, mainly young people. These protests are going to includevisible non-violent resistance to the 3,000 troop surge being headed toIraq. They are acting to create a situation where the U.S. cannotcontinue this illegitimate and illegal war - that deployments not onlystop but that the military withdraws immediately. This town is really intense. It is about 100 degrees outside and incredibly humid. There is a whole military culture throughout the townthat is shaped by unthinking allegiance to the military, and anobsession with the American flag. I have been told that Christianfundamentalism has a firm hold on most people. It is also verydepressing with nothing but strip clubs, bars and fast food chains. Themajority of people here are employed by the military. Some local youthtold me that they have heard reactionary people say that the namestands for Kill Each And Every N*****. I spent the day at Under The Hood Cafe, which is a GI coffeehouse run by anti-war Iraq veterans and others. It was a day of debate anddiscussion, with all of us thinking very deeply about how we can stopthese wars and what should our message be to the people of the world?One Iraq veteran spoke about orders he received to break down the doorsof families and the internal turmoil he went through when he was toldto search an innocent woman's underwear drawer. He got the word “Human”tattooed on his arm after he got out of the military. I talked to ayoung woman who is in her early 20's and did 2 tours of Iraq. She saidthat one of the first things she did when she got out of the militarywas to dye her hair pink. I have a hard time picturing her and any ofthese other people in the military because they have a great deal ofhumanity. She has a lot of urgency to stop these wars and refreshingrefusal to accept the world as it is. She talks about how she wishedthere was some kind of switch you could turn on in people to make themsee the crimes that the military is committing. Many who are here aredealing with pretty heavy PTSD and have trouble sleeping. They talkabout how their bodies have been forever changed by being in themilitary. Those participating in Sunday's action are filled with a deepdesire to tell the truth to people living in this country and people inthe military. |
by John St Clair Akwei fromMindControlForums Website
1. THE NSA'SMISSION AND DOMESTIC INTELLIGENCE OPERATION
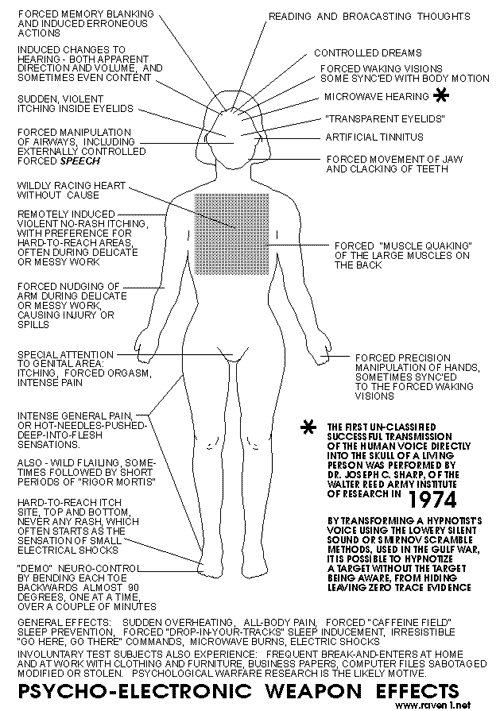
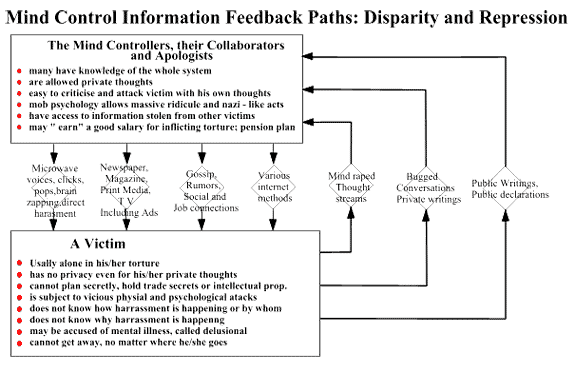
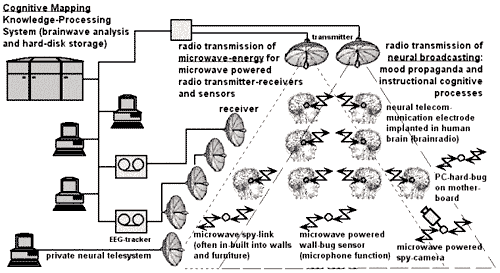
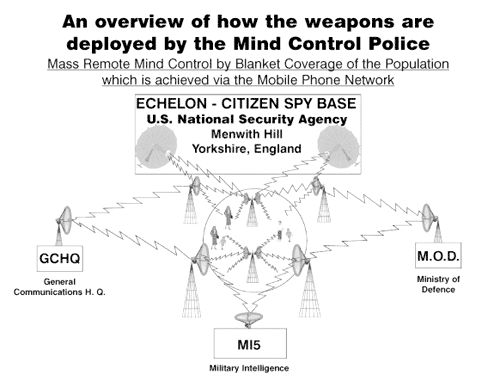
The above symptomshighlight a fraction of the vast array of 2. NSA'SDOMESTIC ELECTRONIC SURVEILLANCE NETWORK At the present time the NSA hasnanotechnology computers that are 15 years ahead of present computertechnology. The NSA obtains blanket coverage of information in theUS by using advanced computers that use artificial intelligence toscreen all communications, regardless of medium, for key words thatshould be brought to the attention of NSA agents/cryptologists. These computers monitor allcommunications at the transmitting and receiving ends. This blanketcoverage of the US is a result of the NSA's Signals Intelligence (SIGINT)mission. The NSA's electronic surveillance network is based on acellular arrangement of devices that can monitor the entire EMF(electromagnetic frequency)spectrum. This equipment was developed, implemented and kept secretin the same manner as other electronic warfare programs.
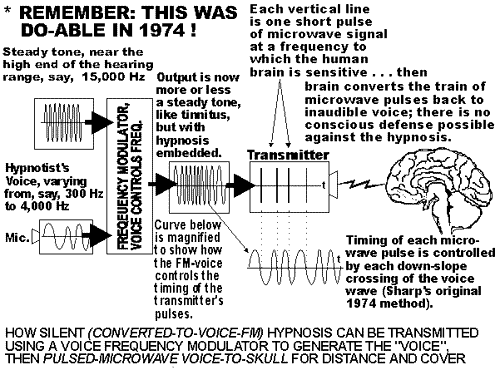
3. NSA SIGNALSINTELLIGENCE USE OF EMF BRAIN STIMULATION EMF BrainStimulation has been in development since theMKULTRA program of theearly 1950s, which included neurological research into radiation(non-ionizing EMF) and bioelectric research and development. Theresulting secret technology is categorized at the National SecurityArchives as "Radiation Intelligence", defined as,
Signals Intelligence implemented andkept this technology secret in the same manner as other electronicwarfare programs of the US Government. The NSA monitors availableinformation about this technology and withholds scientific researchfrom the public. There are also international intelligenceagreements to keep this technology secret. NSA operativescan use this surreptitiously to put images into a surveillancesubject's brain while they are in REM sleep for brain-programmingpurposes.
The above is a simpleflowchart of Nuero-Electromagnetic Frequency Assaults showing methods thatcan be perpetuated by the Police and Military Intelligence Agencies toward Remote MindControl Experiments, Behavioural Manipulation and Murder. 4. NATIONALSECURITY AGENCY SIGNALS INTELLIGENCE ELECTRONIC BRAIN LINKTECHNOLOGY NSA SIGINT can remotely detect, identifyand monitor a person's bioelectric fields. Containedin the electromagnetic emission from the brain are spikes and patternscalled "evoked potentials". Every thought, reaction, motor command,auditory event and visual image in the brain has a corresponding"evoked potential" or set of "evoked potentials". The EMF emission fromthe brain can be decoded into the current thoughts, images and soundsin the subject's brain. It is used by a limitednumber of agents in the US Intelligence Community. The above is a simpleflowchart of Nuero-Electromagnetic Frequency Assaults showing methods thatcan be perpetuated by the Police and Military Intelligence Agenciestoward 5. [NO HEADINGIN ORIGINAL DOCUMENT] That frequency is then modulated in order to imposeinformation in that specific brain area. The frequency to which thevarious brain areas respond varies from 3 Hz to 50 Hz. Only NSASignals Intelligence modulates signals in this frequency band. (SeeTable 1 below) This modulated information can be putinto the brain at varying intensities from subliminal toperceptible. Each person's brain has a unique set of bioelectricresonance/entrainment frequencies. Sending audio information to aperson's brain at the frequency of another person's auditory cortexwould result in that audio information not being perceived. Theyhave also brain-tapped persons the Plaintiff is in contact with tokeep the Plaintiff isolated. This is the first time ever that aprivate citizen has been harassed with RNM and has been able tobring a lawsuit against NSA personnel misusing this intelligenceoperations method. 6. NSATECHNIQUES AND RESOURCES A system forinexpensive implementation of these operations allows for thousandsof persons in every community to be spied on constantly by the NSA.
Editor's Note: I tried ringing MrAkwei to find out what was the out-come, if any, of his court case.He firmly but kindly told me that he could not speak about anythingto do with the case over the phone and hung up. A subsequentconversation of similar length resulted in the information that hedid not wish his address or phone number published with thisarticle. So, if we hear of any developments, we'll let you know.
An example of EMF Brain Stimulation Table 1
RESOURCES When no action was taken against the NSAemployees, I researched the Intelligence Community electronicsurveillance technology involved and discovered the followingpublications.
|
A victory for privacy!
August 6, 2010 at 6:06 pm by Amy E. FerrerToday, the Court of Appeals for the DC Circuit issued a ruling that standsstrongly on the side of privacy and against government intrusion. Fromthe Electronic Frontier Foundation:
The U.S. Court of Appeals for the District of Columbia Circuit today firmly rejected government claims that federal agentshave an unfettered right to install Global Positioning System (GPS)location-tracking devices on anyone’s car without a search warrant. …
“The court correctly recognized the important differences between limited surveillance of public activities possible through visualsurveillance or traditional ‘bumper beepers,’ and the sort of extended,invasive, pervasive, always-on tracking that GPS devices allow,” saidEFF Civil Liberties Director Jennifer Granick. “This same logic appliesin cases of cell phone tracking, and we hope that this decision will befollowed by courts that are currently grappling with the question ofwhether the government must obtain a warrant before using your cellphone as a tracking device.”
“GPS tracking enables the police to know when you visit your doctor, your lawyer, your church, or your lover,” said Arthur Spitzer, LegalDirector of the ACLU-NCA. “And if many people are tracked, GPS datawill show when and where they cross paths. Judicial supervision of thispowerful technology is essential if we are to preserve individualliberty. Today’s decision helps brings the Fourth Amendment into the21st Century.”
Monday, 07 June 2010 20:26
 Illegal Activity Would Violate Nuremberg Code and Could Open Door to Prosecution
Illegal Activity Would Violate Nuremberg Code and Could Open Door to Prosecution
- Research and medical experimentation on detainees was used to measure theeffects of large- volume waterboarding and adjust the procedureaccording to the results. After medical monitoring and advice, the CIAexperimentally added saline, in an attempt to prevent putting detaineesin a coma or killing them through over-ingestion of large amounts ofplain water. The report observes: “‘Waterboarding 2.0’ was the productof the CIA’s developing and field-testing an intentionally harmfulpractice, using systematic medical monitoring and the application ofsubsequent generalizable knowledge.”
- Health professionals monitored sleep deprivation on more than a dozendetainees in 48-, 96- and 180-hour increments. This research wasapparently used to monitor and assess the effects of varying levels ofsleep deprivation to support legal definitions of torture and to planfuture sleep deprivation techniques.
- Health professionals appear to have analyzed data, based on their observationsof 25 detainees who were subjected to individual and combinedapplications of “enhanced” interrogation techniques, to determinewhether one type of application over another would increase thesubject’s “susceptibility to severe pain.” The alleged research appearsto have been undertaken only to assess the legality of the “enhanced”interrogation tactics and to guide future application of the techniques.















 By Emma Kaplan
By Emma Kaplan